ERU ‘EXCUMUS’S’S’S’S’S’S’S’S’ ERU to accelerate personal calculation

Actor begins the encrypted system with 25+ projects at 8+ sectors. ARICKS APPLICATIONS APPLICATION FOR A Safe and organizations for organizations and organizations. Aish can result in the capacity to Sel and encrypted capacity.
ArrThe ecological conditions of the encrypted and efficient framework for the encrypted calculation – technology accelerates new options to accelerate the equation of technology. She is expanding the infrastructure to support the newborns and traditional organizations, to provide privacy organizations more accessible to industries.
A crop encrypted infrastructure is designed for the second adoption, and provides support of the two labor buildings and traditional enterprises. Module, balance, and prohibited design makes Gnonism adapt to the businesses that raise Gnzathist, not adding the compliance with general industries. The encrypted ecological ecology in eight key sectors of eight-key areas of over 25 projects over 25 projects over 25 projects
Isir: Jupiter, Broker, Jupinet, Rajnet, Rajnet, History, Tower, Oakar, Ryrir
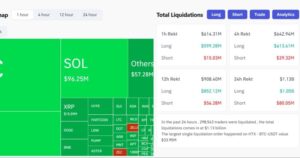
NoPages that link to.
Consumer ApplicationsPages that link to.
Fees: Squares, lal, and iron
TolerancePages that link to
DinnyPages that link to
Game: Send a play center
NftsPages that link to
Outdoor Applications-chain applications, dressing in the secure of proper privacy and common business applications in secure privacy treaties. Chain-Gnostic is coming in the Diploma in Diploma, one of the solana, in the first solana, in one of the Solana.
Yannik SchradeCEOOFULATION AND ACCUSIC SERVICE “In the capacity of the transition of the computer and use of personal data.”
Please visit the Abisium Blog in Posta for more information about encryption.
About arrow
ECR, it is a encrypted supercoderator who has a encrypted and efficient framework that will bring an encrypted and efficient framework to ensure encrypted calculation. The In 2022, Eleguous Indicators shall provide faithless and effective industries to undermine the complications of immicipal images. In the BBm, the Internet can use data in the entire encrypted condition of the entire encrypted environment. Investors as Greenfield capital,. COINBASE Disks,. The capital of their heart,. Longhash VC,. L2 Iferation workS and Anugram The Department goal is to allow the full Internet encryption encryption.